The blog is dedicated to providing data to researchers, students and professionals, and adding fun to delivering information to our audience.
اعلان test
الخميس، 31 أغسطس 2017
COMBATING CLOUD SECURITY THREATS: TOOLS AND BEST PRACTICES
COMBATING CLOUD SECURITY THREATS: TOOLS AND BEST PRACTICES
written by Sekhar Sarukkai August 24, 2017
Now more than ever, the cloud plays a vital role in business. Cloud services are deployed in almost every environment, and they’re integrated at almost every level. Also, as with any business technology, cloud services need protection.
Cloud-service use is expanding, too. In 2016 alone, organizations used 1,427 cloud services, a 23.7 percent increase from 2015. Although this level of growth and adoption is encouraging for cloud providers, risks are also associated with the expanding cloud. Underscoring this fact, IT security is only aware of about 10% of cloud-service usage; the other 90% falls in the shadow-IT category.
Sensitive information, such as personally identifiable information (PII) and intellectual property, constitutes 18 percent of the data uploaded to cloud applications. Companies currently experience 23 cloud security threats per month, an increase of 18.4 percent since last year. This situation makes the cloud especially risky, since insider-caused data leaks are also on the rise.
The Dangers of Shadow IT
Part of the risk associated with insider threats relates to shadow IT: employee use of cloud services that are unapproved by the organization. An example of a risky shadow-IT program is a PDF converter with a terms of use that says any file or data uploaded to their cloud becomes the property of the provider. Although IT security departments will vet cloud applications by weighing the security risks and built-in capabilities of the cloud application, rarely do employees apply the same level of scrutiny.
Avoiding the Threats
Despite the risks of using cloud services, the benefits mean organizations must adopt cloud-governance strategies to deal with the potential security issues. A cloud-governance strategy allows enterprises to reap the benefits of cloud computing without putting sensitive corporate data at risk.
Cloud-Security Best Practices
The following best practices promote better security when using cloud-based services.
1. Visibility
Knowing what cloud applications employees are using should be the starting point. When you know what cloud services are in use, you can develop a more effective plan to secure them. Additionally, IT security should be able to answer questions such as, Does the cloud service encrypt data at rest? Does it delete user data on account termination? And does it provide multifactor authentication? Such questions will enable IT security to selectively allow cloud services that boost productivity while blocking less reputable cloud applications that put corporate data at risk.
2. Threat Prevention
The average enterprise will generate billions of events in the cloud daily. Most will be typical events such as an employee downloading a file from a file-sharing service. A tiny fraction of these events, however, will be anomalous enough to warrant further investigation.
For example, if an employee logs into Salesforce from Chicago and then, within minutes, logs into the same account from Shanghai, this type of anomalous event should be flagged for further investigation because it may be a sign of a compromised account. Effectively detecting cloud threats while ignoring normal events requires machine learning that can ingest and analyze massive amounts of data.
Enterprises looking to detect and prevent cloud threats (from insiders or malicious outsiders) while minimizing false positives should combine their non-cloud events with cloud-generated events. These events should then be sent to the company’s security and operations center (SOC) to avoid siloed threat prevention.
3. Data Security
Data security can take on a number of forms. Two commonly used methods for securing data in the cloud are encryption and tokenization. Both have advantages and disadvantages. Encryption can be an effective means of protecting data as long as the decryption keys don’t fall in the wrong hands. Tokenization, on the other hand, randomly generates a token value for plain text and stores the mapping in a database. With tokenization, the sensitive information never leaves an organization; if the token vault is hacked, though, data can be detokenized and exposed to a breach.
Tokenization is best suited to securing structured information such as payment-card data, whereas encryption can secure unstructured information such as a word document containing intellectual property.
An important thing to remember regarding encryption is that although many cloud providers offer it, they have access to the decryption key. Organizations should instead use encryption where they, and only they, have access to the decryption key.
4. Cloud Compliance
The proliferation of cloud services means enterprises must rethink how they will comply with federal, international and regional regulations, such as HIPAA-HITECH, PCI-DSS and the upcoming E.U. GDPR.
Traditionally, organizations have relied on data-loss-prevention (DLP) tools to ensure they comply with applicable policies. When applying DLP to the cloud, they must ensure they apply the same set of policies that protects data on the company premises to the cloud. To do so, organizations should take the following steps:
- Inventory existing policies and define cloud-specific policies
- Understand what types of sensitive data are being uploaded to the cloud (Social Security numbers, health records, account numbers, credit-card numbers and so on)
- Understand who is collaborating in the cloud with access to sensitive data
- Prevent sharing of sensitive data with unauthorized third parties
- Prevent high-value data from being uploaded to or stored in the cloud
- Enforce consistent DLP policies across all cloud services
Effective Cloud-Security Tools
A number of tools can assist you in your cloud-security project:
- Cloud firewall: For low-level threats, a cloud firewall can provide a stable security layer between the network and the cloud.
- Cloud data encryption: By encrypting sensitive data, you make it much harder for hackers to gain unauthorized access.
- User access control: Follow the principle of “right of least privilege,” giving the users what they need to do their job and no more.
- CASBs: Cloud-access security brokers can offload security-monitoring processes and provide reports based on thresholds you establish.
- Platform providers: Most cloud providers have more than just one solution and can offer a complete integrated security platform.
It’s increasingly impossible to operate in today’s business environment without a comprehensive cloud-security strategy. By following the best practices outlined above, you can start reaping the benefits of cloud computing while minimizing the risks.
الأربعاء، 30 أغسطس 2017
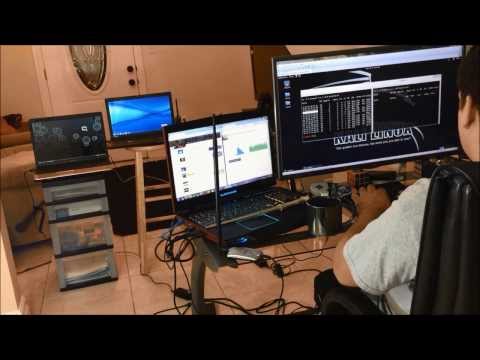
Five-Monitor Arc
Five-Monitor Arc
The Boston office of Mitch Haile is a great introduction to the world of seriously overpowered home offices. Haile, a software developer, built this workspace in 2011 around a U-shaped desk in the attic of his house, which helped him grind through 60-80 hours a week writing code. One side of the desk boasted a quintet of monitors that allow him unprecedented screen space, hooked up to a 12-core Mac Pro with a grotesque 50TB of storage space. This guy's into some serious projects. Unfortunately for fans of epic displays, Haile has cut back on the real estate of his setup and is now rocking a mere three monitors.
الاشتراك في:
الرسائل (Atom)
-
Bespoke Heating Elements from Tecnologic UK Bespoke Heating Elements from Tecnologic UK Tecnologic UK specialise in bespoke ...